Table Of Content
60% of breaches exploit gaps in single-layer defenses. This gives a clear and urgent picture of today’s security. This is where relying on just one line of protection is not enough. The year 2025 brought an evolved cyber threat landscape. We see that AI-driven attacks are capable of bypassing traditional defenses. And this happens in seconds. Where we find tremendous scalability, we also find new vulnerability windows opened.
Cloud adoption has simultaneously increased the need for better defenses. Since cybercriminals eagerly exploit the networks. Meanwhile, remote work, Internet of Things (IoT) devices, and decentralized environments ensured the safety of sensitive data. Since it is constantly moving, so are the threats chasing it.
Why a Multi-Tiered Defense is Essential in 2025
Organizations can no longer afford reactive security models. And, single-point defenses also don’t meet the need in that case. To survive, they must move toward proactive, adaptable strategies. Here is where layered security comes in. It is one of the most critical evolutions in cybersecurity.
A strategy that creates multiple interlocking barriers. It protects an organization’s assets from all sides. This ensures that even if one line of defense fails, your whole system will not crash. Attackers still will have numerous additional obstacles to overcome. If you’re serious about protecting your organization in 2025. Then, you must go beyond merely setting up a firewall. You need to build a stronger defense system, layer by layer.
What is Layered Security?
Layered security is also referred to as defense in depth. It is built on the principle of not relying on a single point of failure. Every security measure has limitations. Here, firewalls can be bypassed. We also see that passwords can be cracked. Additionally, anti-virus software can miss zero-day threats. How to deal with this? Simple, combine these tools into a comprehensive, multi-tiered security strategy. This way the weaknesses of one are covered by the strengths of another.
Think of layered security like the defense systems of a castle. Just a thick wall can’t always protect it. It needs multiple layers of defense. Even if one barrier is breached, attackers would still face significant resistance. This will repeat with every next barrier. Each layer covers what the others might miss. This collectively creates a near-impenetrable defense.
Layered security in cybersecurity functions like this. Multiple defense mechanisms work together. Each of them addresses different types of threats. The more barriers an attacker must overcome. The less likely they are to succeed. This gives defenders more time to detect and respond.
Key Layers of Protection
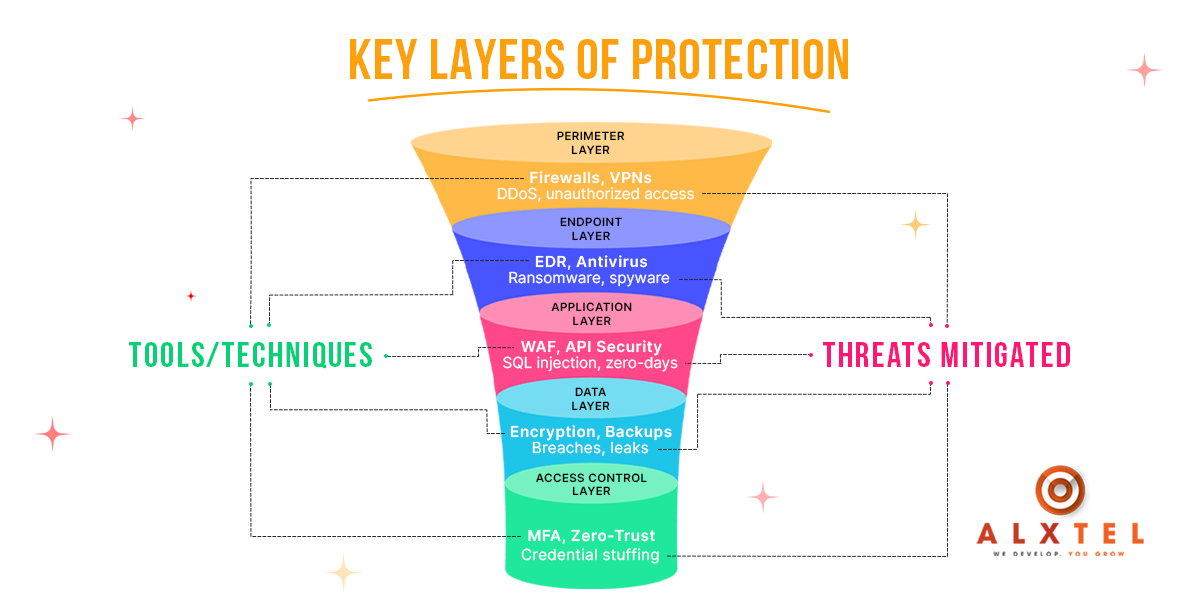
An effective layered security strategy doesn’t happen by accident. It requires a deliberate combination of tools and techniques. Hence, each is designed to tackle some specific types of threats. While there are many ways to structure layers. The most critical categories typically following factors. These are perimeter, endpoint, application, data, and access control protections.
What does the perimeter layer do? It defends the boundaries of your network. What plays an important role here? Firewalls and Virtual Private Networks (VPNs). The Firewalls monitor incoming and outgoing traffic. They are responsible for allowing or blocking packets based on security rules. Meanwhile, VPNs encrypt traffic. This ensures their protection from interception. These tools help prevent the attacks. Major of those attacks include Distributed Denial of Service (DDoS) attacks and unauthorized access attempts. This ensures that external threats have a harder time reaching your network’s core.
Layered Security through the Network
The endpoint layer focuses on individual devices. All the devices that connect to your network are included. With remote work and BYOD policies becoming the norm. We see that securing endpoints has become more critical. This includes Endpoint Detection and Response (EDR) systems and antivirus software as actively participating. They monitor and neutralize threats like ransomware and spyware. They target devices directly, hence layered security focuses on them.
The application layer protects the software your organization relies on. This includes web apps and APIs, especially. What do Web Application Firewalls (WAFs) do? They filter, monitor, and block HTTP traffic to and from a web application. Hence, API security tools prevent threats. These threats can be SQL injection and zero-day vulnerabilities. Such threats can exploit application flaws to access sensitive data.
The data layer safeguards the information itself, regardless of where it resides. Encryption, whether in transit or at rest, ensures that even if data is intercepted, it remains unreadable without the decryption keys. Regular backups ensure resilience against breaches and ransomware attacks by allowing organizations to quickly restore compromised systems.
Finally, the access control layer governs who can get into your systems and how. Multi-Factor Authentication (MFA) adds a second layer of security beyond passwords, while Zero-Trust frameworks assume that no entity, whether inside or outside the network, should automatically be trusted. These tools are critical for preventing credential stuffing attacks and unauthorized internal access.
Together, these layers create a comprehensive, interlocking defense that makes breaching your organization’s security exponentially more difficult.
Layered Security + Zero-Trust = Unbeatable
While layered security provides multiple barriers to entry, integrating Zero-Trust principles makes your defense almost impenetrable. Recent studies show that implementing Zero-Trust strategies reduces the financial impact of breaches by nearly 50%. This is because Zero-Trust fundamentally shifts the security model: it requires verification for every access request, regardless of where it originates, and treats every device, user, and connection as potentially compromised until proven otherwise.
Zero-Trust is not a product—it’s a mindset. It assumes that threats could already be inside your network and demands constant verification of identities, devices, and activities. This approach works beautifully with layered security because where layered defenses isolate and compartmentalize threats, Zero-Trust verifies and validates every interaction at every point. Together, they create a system where attackers not only have to breach multiple barriers but also prove themselves at every step—a daunting, often impossible task.
Real-World Applications
In real-world scenarios, the need for layered security is even more evident, especially in cloud environments and remote work settings. Public cloud platforms like AWS, Azure, and Google Cloud offer enormous flexibility, but they also expand your attack surface. Layered security strategies are vital here: perimeter firewalls control access to cloud workloads, endpoint protections safeguard connected devices, application security tools protect APIs, and encryption ensures that data remains safe even in a shared infrastructure.
Similarly, remote work, which has become standard practice for many organizations, introduces new vulnerabilities through employee-owned devices and home networks. Securing remote workers requires endpoint protection solutions like EDR, secure VPNs for encrypted connections, application layer security for SaaS tools, and strict access controls that limit who can reach critical systems and under what circumstances. A single layer isn’t enough because threats can arise from device theft, phishing attacks, unsecured Wi-Fi, or even insider threats. Layered security ensures that there’s a protective net no matter where the attack originates.
Common Pitfalls (And How to Avoid Them)
Despite the clear benefits, organizations often make critical mistakes when implementing layered security. One of the most common is over-reliance on firewalls. Firewalls are an essential perimeter defense, but they cannot detect threats that are already inside your network or stop sophisticated phishing campaigns targeting employees directly. Believing that a firewall alone will save you is like putting a lock on your front door while leaving the windows wide open.
Another common pitfall is neglecting employee training. The most sophisticated cybersecurity system in the world can be undone by a single careless click. Social engineering remains one of the easiest ways for attackers to breach organizations. Regular cybersecurity awareness training ensures that employees recognize phishing attempts, understand the importance of strong passwords, and follow best practices when handling sensitive data.
Failing to regularly update and test your security layers is another major mistake. Cyber threats evolve daily. What worked last year may already be obsolete today. Regularly updating software, conducting penetration testing, and simulating attack scenarios ensures that your defenses stay resilient and responsive.
Finally, organizations sometimes deploy overlapping security tools that create unnecessary complexity without adding real protection. Every layer should be purposeful, strategically selected to address a specific threat without bogging down operations or creating blind spots through overcomplication.
Frequently Asked Questions
What is layered security in cybersecurity?
Layered security is a defense strategy that uses multiple security measures to protect information across different points of vulnerability. This ensures that if one measure fails, others still stand to protect the system.
How does defense in depth differ from traditional cybersecurity?
Traditional cybersecurity often relies heavily on perimeter defenses like firewalls. Defense in depth, or layered security, assumes that threats can breach any single defense and therefore establishes multiple, redundant layers to detect and stop threats at different stages.
Why combine Zero-Trust with layered security?
Zero-Trust focuses on verifying every action within a network, assuming that no device or user is inherently trustworthy. When combined with layered security, this approach adds dynamic verification to a robust physical and logical defense system, significantly reducing the chances of successful breaches.
Is layered security only necessary for large enterprises?
No. Every organization, regardless of size, benefits from layered security. In fact, small and medium businesses are often targeted precisely because attackers expect weaker defenses. A properly layered security strategy provides critical resilience at any scale.
How can organizations implement layered security effectively?
Organizations should begin by assessing their specific threat landscape, identifying critical assets, and deploying strategic layers—perimeter defenses, endpoint protections, application security, data safeguards, and access control measures—tailored to their operational environment. Regular testing, updates, and employee training are essential to maintain effectiveness.
References
Need support? You are our priority, We’ve got you covered.
Rapid response time to service requests, responding to all customer feedback to get in touch.
Our goal is to supply you with the best possible customer service across all our products and solutions. We look forward to helping you make the most of your AlxTel platform.